Tuesday, 30 April 2019
Monday, 29 April 2019
Friday, 26 April 2019
Thursday, 25 April 2019
Wednesday, 24 April 2019
Tuesday, 23 April 2019
WIPRO IS HACKED!

ORIGINAL CONTENT: https://www.securitynewspaper.com/2019/04/16/wipro-is-hacked/
Looks impossible but tech giant is under attack. According to cyber forensic researcher of International Institute of Cyber Security, a serious break into the networks and Systems are being used to launch attack on customers. The cyber attack was forcing tech outsourcing giant to develop private mail service to replace compromised systems of corporate.
Sources of security researchers told that Wipro compromised systems are being used as launchpad for attacking on outsources customers. Customers of Wipro, traced suspicious traffic, communicating back to partner system directly with outsources corporate network.
According to cyber forensic researcher of international institute of cyber security eleven companies have been under cyber attacked. But still it not cleared which ones.
Wipro spokes person said that Wipro has system of advance security technology to detect & protect from cyber attacks & monitor companies entire infrastructure.
RECENT WIPRO STATEMENT SAYS THAT :
- Cyber forensics investigation teams has detected abnormal activity in few employees accounts on companies network.
- After cyber attack company has learned a lot, and began an top priority investigation to find affected users.
- Further company spokesperson said, We will contact our industry leading cyber security experts with our partner ecosystem to acquire and monitor advanced threat intelligence for enhancing our security.
- Wipro has also contacted to independent forensic firm to assist in investigation & will continue to monitor their network & infrastructure.
WIPRO IS HACKED!

ORIGINAL CONTENT: https://www.securitynewspaper.com/2019/04/16/wipro-is-hacked/
Looks impossible but tech giant is under attack. According to cyber forensic researcher of International Institute of Cyber Security, a serious break into the networks and Systems are being used to launch attack on customers. The cyber attack was forcing tech outsourcing giant to develop private mail service to replace compromised systems of corporate.
Sources of security researchers told that Wipro compromised systems are being used as launchpad for attacking on outsources customers. Customers of Wipro, traced suspicious traffic, communicating back to partner system directly with outsources corporate network.
According to cyber forensic researcher of international institute of cyber security eleven companies have been under cyber attacked. But still it not cleared which ones.
Wipro spokes person said that Wipro has system of advance security technology to detect & protect from cyber attacks & monitor companies entire infrastructure.
RECENT WIPRO STATEMENT SAYS THAT :
- Cyber forensics investigation teams has detected abnormal activity in few employees accounts on companies network.
- After cyber attack company has learned a lot, and began an top priority investigation to find affected users.
- Further company spokesperson said, We will contact our industry leading cyber security experts with our partner ecosystem to acquire and monitor advanced threat intelligence for enhancing our security.
- Wipro has also contacted to independent forensic firm to assist in investigation & will continue to monitor their network & infrastructure.
Monday, 22 April 2019
Wednesday, 17 April 2019
Tuesday, 16 April 2019
TELEGRAM TON BLOCKCHAIN NETWORK, ALTERNATIVA DE TOR, SERÁ LANZADA PRONTO

CONTENIDO ORIGINAL: https://noticiasseguridad.com/seguridad-informatica/telegram-ton-blockchain-network-alternativa-de-tor-sera-lanzada-pronto/
El servicio de mensajería instantánea Telegram lanzará una prueba beta privada de su blockchain, Telegram Open Network (TON, reportan expertos en cómputo forense del Instituto Internacional de Seguridad Cibernética (IICS).
Características
Telegram Open Network está diseñado para tener una velocidad y escalabilidad superiores. En primer lugar, esto significa que puede procesar millones de transacciones en segundos. Además, la red puede alojar millones de transacciones activas y millones de aplicaciones sin comprometer su escalabilidad.
Acorde a los expertos en cómputo forense, las principales blockchain (Bitcoin y Ethereum) realizan 7 y 15 transacciones por segundo, respectivamente. Esta capacidad hace que estas redes sean apenas suficientes para reemplazar tecnologías como Mastercard y VISA. Además, esta restricción aumenta los costos de transacción. La velocidad y escalabilidad de TON es una solución viable que satisface esta necesidad de la comunidad.
Facilidad de uso
Telegram Open Network ejecuta interfaces de usuario intuitivas que facilitan a los usuarios el pedido, la venta y la transferencia de valor. Además, las funciones intuitivas hacen que las aplicaciones descentralizadas se ejecuten sin inconvenientes. Estas capacidades intuitivas proporcionan una capacidad de respuesta superior, un uso sin esfuerzo por parte del usuario y operaciones interactivas.
TON Proxy
La privacidad en línea es un tema muy controvertido y, por el momento, carece de una legislación formal a la cual haya qué apegarse. Acorde a expertos en cómputo forense del Instituto Internacional de Seguridad Cibernética (IICS), demasiada legislación puede considerarse como censura, en cambio, la carencia de regulación es un espacio abierto a las actividades criminales.
TON Proxy, o anomymizer, ha sido diseñado para proteger la privacidad del usuario mientras navega por Internet, garantizando su anonimato. TON Proxy ofrece características de Tor: oculta direcciones IP y oculta la identidad del usuario. Gracias a TON DNS y TON P2P Network, puede hacer imposible la censura en cualquier servicio, incluido Telegram.
TON es una tecnología que proporciona un sistema de almacenamiento de archivos. Un beneficio fundamental de esta tecnología es su acceso tipo torrent, que admite el intercambio de archivos P2P, lo que significa que el sistema no depende de una sola persona para entregar un archivo. Para recibir un álbum, por ejemplo, en lugar de que el producto sea entregado por un sólo individuo, éste se entrega por un grupo de personas (o enjambre), lo que reduce el tiempo de espera para recibir archivos y los costos para los usuarios. El almacenamiento TON también implementa tecnología de contratos inteligentes para administrar aplicaciones descentralizadas que requieren grandes capacidades de almacenamiento.
TON proporciona una plataforma que permite la prestación fácil de servicios de terceros al público en general. Los desarrolladores que pretenden proporcionar aplicaciones y servicios descentralizados que se ejecutan en contratos inteligentes pueden beneficiarse.
TON Services proporcionan una interfaz similar a un smartphone que es amigable para el usuario y cuenta con una experiencia de navegación descentralizada similar a la navegación por la web.
TELEGRAM TON BLOCKCHAIN NETWORK, ALTERNATIVA DE TOR, SERÁ LANZADA PRONTO

CONTENIDO ORIGINAL: https://noticiasseguridad.com/seguridad-informatica/telegram-ton-blockchain-network-alternativa-de-tor-sera-lanzada-pronto/
El servicio de mensajería instantánea Telegram lanzará una prueba beta privada de su blockchain, Telegram Open Network (TON, reportan expertos en cómputo forense del Instituto Internacional de Seguridad Cibernética (IICS).
Características
Telegram Open Network está diseñado para tener una velocidad y escalabilidad superiores. En primer lugar, esto significa que puede procesar millones de transacciones en segundos. Además, la red puede alojar millones de transacciones activas y millones de aplicaciones sin comprometer su escalabilidad.
Acorde a los expertos en cómputo forense, las principales blockchain (Bitcoin y Ethereum) realizan 7 y 15 transacciones por segundo, respectivamente. Esta capacidad hace que estas redes sean apenas suficientes para reemplazar tecnologías como Mastercard y VISA. Además, esta restricción aumenta los costos de transacción. La velocidad y escalabilidad de TON es una solución viable que satisface esta necesidad de la comunidad.
Facilidad de uso
Telegram Open Network ejecuta interfaces de usuario intuitivas que facilitan a los usuarios el pedido, la venta y la transferencia de valor. Además, las funciones intuitivas hacen que las aplicaciones descentralizadas se ejecuten sin inconvenientes. Estas capacidades intuitivas proporcionan una capacidad de respuesta superior, un uso sin esfuerzo por parte del usuario y operaciones interactivas.
TON Proxy
La privacidad en línea es un tema muy controvertido y, por el momento, carece de una legislación formal a la cual haya qué apegarse. Acorde a expertos en cómputo forense del Instituto Internacional de Seguridad Cibernética (IICS), demasiada legislación puede considerarse como censura, en cambio, la carencia de regulación es un espacio abierto a las actividades criminales.
TON Proxy, o anomymizer, ha sido diseñado para proteger la privacidad del usuario mientras navega por Internet, garantizando su anonimato. TON Proxy ofrece características de Tor: oculta direcciones IP y oculta la identidad del usuario. Gracias a TON DNS y TON P2P Network, puede hacer imposible la censura en cualquier servicio, incluido Telegram.
TON es una tecnología que proporciona un sistema de almacenamiento de archivos. Un beneficio fundamental de esta tecnología es su acceso tipo torrent, que admite el intercambio de archivos P2P, lo que significa que el sistema no depende de una sola persona para entregar un archivo. Para recibir un álbum, por ejemplo, en lugar de que el producto sea entregado por un sólo individuo, éste se entrega por un grupo de personas (o enjambre), lo que reduce el tiempo de espera para recibir archivos y los costos para los usuarios. El almacenamiento TON también implementa tecnología de contratos inteligentes para administrar aplicaciones descentralizadas que requieren grandes capacidades de almacenamiento.
TON proporciona una plataforma que permite la prestación fácil de servicios de terceros al público en general. Los desarrolladores que pretenden proporcionar aplicaciones y servicios descentralizados que se ejecutan en contratos inteligentes pueden beneficiarse.
TON Services proporcionan una interfaz similar a un smartphone que es amigable para el usuario y cuenta con una experiencia de navegación descentralizada similar a la navegación por la web.
Monday, 15 April 2019
Friday, 12 April 2019
Thursday, 11 April 2019
Wednesday, 10 April 2019
Tuesday, 9 April 2019
Monday, 8 April 2019
Friday, 5 April 2019
Thursday, 4 April 2019
Wednesday, 3 April 2019
Tuesday, 2 April 2019
CÓMO AUTOMATIZAR LA FASE INICIAL DE PENTESTING
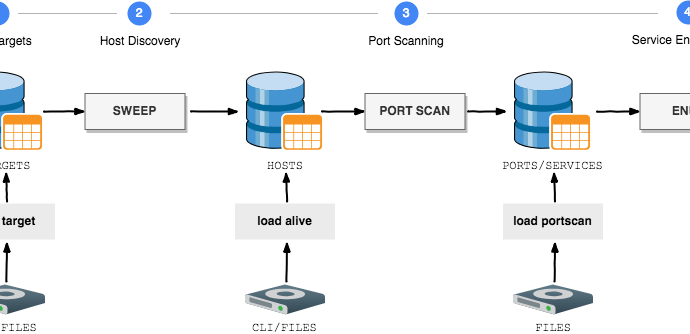
CONTENIDO ORIGINAL: https://noticiasseguridad.com/tutoriales/como-automatizar-la-fase-inicial-de-pentesting/
En el pentesting se utilizan diferentes técnicas manuales y automáticas según la aplicación web que se esté analizando. Los pentesters tratarán de encontrar las vulnerabilidades de seguridad en el código fuente o en los puertos vulnerables. Investigadores en hacking ético del Instituto Internacional de Seguridad Cibernética (IICS) demostraron recientemente una vulnerabilidad crítica gracias a una herramienta llamada GOscan, misma que presentaremos a continuación.
GOscan es un escáner de red que proporciona automatización durante este procedimiento. Esta herramienta se usa para encontrar puertos y servicios abiertos en el objetivo de nuestras pruebas. GOscan es compatible con todas las características principales de enumeración. Esta herramienta usa bases de datos SQLite durante el escaneo.
Acorde a los investigadores en hacking ético del IICS, GOscan puede ser una herramienta funcional en distintas fases del pentesting.
- Del lado del atacante, Goscan ha sido probado en Kali Linux 2018.4 amd64. Y para el objetivo hemos utilizado DVWA
- Descargar DVWA desde http://www.dvwa.co.uk/DVWA-1.0.7.iso
- Abra DVWA-1.0.7.iso en vmware. Abrir Vmware haga clic en abrir. Ir a la ubicación donde ha descargado DVWA iso. Seleccione que iso & abrir en Vmware
- Haga clic en Encender en la máquina virtual. Escriba ifconfig para saber la dirección IP; abra el navegador y escriba DVWA ip address
- Por defecto el nombre de usuario DVWA: admin y contraseña: password
- DVWA ya está configurada. Después de configurar el objetivo, ahora configura GOscan
- Esta herramienta se basa en el entorno GO. Si GO no está instalado, descargue y configure GO antes de usar GOSCAN
- Para descargar GO, escriba: wget https://dl.google.com/go/go1.12.1.linux-amd64.tar.gz
root@kali:/home/iicybersecurity# wget https://dl.google.com/go/go1.12.1.linux-amd64.tar.gz --2019-03-18 02:21:59-- https://dl.google.com/go/go1.12.1.linux-amd64.tar.gz Resolving dl.google.com (dl.google.com)… 172.217.167.14, 2404:6800:4002:80a::200e Connecting to dl.google.com (dl.google.com)|172.217.167.14|:443… connected. HTTP request sent, awaiting response… 200 OK Length: 127906702 (122M) [application/octet-stream] Saving to: ‘go1.12.1.linux-amd64.tar.gz’ go1.12.1.linux-amd64.tar.gz 100%[===========================================================>] 121.98M 1.89MB/s in 93s 2019-03-19 12:48:43 (1.31 MB/s) - ‘go1.12.1.linux-amd64.tar.gz’ saved [127906702/127906702]
- Escriba tar -xvzf go1.12.1.linux-amd64.tar.gz
- Escriba cd go y cd bin
- Copie el tipo de archivo go cp go / usr / local / bin / go
- Escriba export GOROOT = / home / iicybersecurity / go / bin
- Escriba echo $ GOROOT
root@kali:/home/iicybersecurity/Downloads# export GOROOT=/home/iicyberseurity/go/bin root@kali:/home/iicybersecurity/Downloads# echo $GOROOT /home/iicyebrsecurity/go/bin
- Después de instalar teclee wget https://github.com/marco-lancini/goscan/releases/download/v2.4/goscan_2.4_linux_amd64.zip
- Escriba unzip goscan_2.4_linux_amd64.zip
- Escriba chmod u + x goscan
- Escriba ./goscan
root@kali:/home/iicybersecurity/Downloads# ./goscan
__ ____/_______ ___/_ ____/__ |__ | / /
_ / __ _ __ \____ \_ / __ /| |_ |/ /
/ /_/ / / /_/ /___/ // /___ _ ___ | /| /
\____/ \____//____/ \____/ /_/ |_/_/ |_/
goscan (v.2.4)
Marco Lancini [@LanciniMarco]
- Antes de ejecutar un análisis, agregue la dirección IP de destino en la base de datos de GOscan. Escriba load target SINGLE 192.168.1.105
- También puede agregar múltiples direcciones IP en la base de datos de goscan. Escriba load target MULTIPLE /home/iicybersecurity/Downloads/Iplist.txt y seleccione el txt que contiene las direcciones IP
- Escriba show targets para comprobar las direcciones IP agregadas
[goscan] > load target SINGLE 192.168.1.9 [*] Imported target: 192.168.1.9 [goscan] > show targets +---------------+------------+ | ADDRESS | STEP | +---------------+------------+ | 192.168.1.105 | IMPORTED | +---------------+------------+
- Antes de encontrar cualquier servicio o puerto en las direcciones IP de destino. GOSCAN necesita hacer ping en la dirección IP agregada
- Cada pentesting se inicializa con PING (Packet Internet Groper) es la utilidad más común que se utiliza para verificar la disponibilidad en Internet. Así que goscan también comprueba con ping. Para comprobar escriba sweep PING 192.168.1.105
[goscan] > sweep PING 192.168.1.105 [] Starting Ping Sweep [goscan] > [-] Created directory: /root/.goscan/192.168.1.105/sweep [-] Executing command: nmap -n -sn -PE -PP 192.168.1.105 -oA /root/.goscan/192.168.1.105/sweep/ping_192.168.1.105 [] [ping] Nmap work in progress on host: 192.168.1.105 [+] [ping] Nmap finished on host: 192.168.1.105 [+] [ping] Output has been saved at: /root/.goscan
- Escriba show targets para comprobar los objetivos disponibles
[goscan] > show targets +------------------+----------+ | ADDRESS | STEP | +------------------+----------+ | 192.168.1.105 | SWEEPED | +------------------+----------+
Escaneo TCP
- Escriba portscan TCP-FULL 192.168.1.105portscan encontrará puertos abiertos del destino. GOscan ofrece escaneo TCP y UDP
- Hemos utilizado TCP-FULL scan en el que goscan usará los protocolos de red más comunes
GOscan buscará:
- TCP-ESTÁNDAR: búsqueda de los mejores 200 TCP-SCAN
- TCP-PROD: escanea el protocolo T3 RMI (Invocación de método remoto) que se usa para transformar información entre weblogic y otros programas
- TCP-VULN SCAN: busca scripts nse enumerados en CVE e intenta encontrar vulnerabilidades en la dirección IP
- Luego escriba la dirección IP de destino 192.168.1.105
[goscan] > portscan TCP-FULL 192.168.1.105 [] Starting full TCP port scan [goscan] > [-] Executing command: nmap -Pn -sT -sC -A -T4 -p- 192.168.1.105 -oA /root/.goscan/192.168.1.105/portscan/tcp_full_192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [+] [tcp_standard] Nmap finished on host: 192.168.1.105 [+] [tcp_standard] Output has been saved at: /root/.goscan [+] [tcp_standard] Nmap finished on host: 192.168.1.105 [+] [tcp_standard] Output has been saved at: /root/.goscan
- Después de ejecutar la consulta anterior, se muestra cómo nmap utiliza diferentes consultas para buscar puertos abiertos. Después de que las exploraciones hayan completado, escriba show ports para mostrar la lista de puertos abiertos en la dirección IP
[goscan] > show ports +----------------+----------+----------+---------------------------------------------+ | HOST | PORT | STATUS | SERVICE | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 21/tcp | open | ftp [ProFTPD 1.3.2c] [Unix] | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 22/tcp | open | ssh [OpenSSH 5.3p1 Debian 3ubuntu4] [Linux] | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 80/tcp | open | http [Apache httpd 2.2.14] | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 443/tcp | open | http [Apache httpd 2.2.14] | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 3306/tcp | open | mysql [MySQL ] | +----------------+----------+----------+---------------------------------------------+
- Arriba se muestran los puertos abiertos del objetivo. Los anteriores son los puertos más comunes que se utilizan durante la exploración
- Goscan también guarda la salida al crear un directorio de direcciones IP escaneadas.
- Para acceder al directorio escriba cd /root/.goscan
- Escriba cd 192.168.1.105
- Escriba ls & cat tcp_full_192.168.1.105.nmap
root@kali:~/.goscan/192.168.1.105/portscan# ls tcp_full_192.168.1.105.nmap root@kali:~/.goscan/192.168.1.105/portscan# cat tcp_full_192.168.1.105.nmap Nmap 7.70 scan initiated Tue Mar 26 03:33:34 2019 as: nmap -Pn -sT -sC -A -T4 -p- -oA /root/.goscan/192.168.1.105/portscan/tcp_full_192.168.1.105 192.168.1.105 Nmap scan report for dvwa (192.168.1.105) Host is up (0.0011s latency). Not shown: 65530 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp ProFTPD 1.3.2c 22/tcp open ssh OpenSSH 5.3p1 Debian 3ubuntu4 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.2.14 ((Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1) | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set | http-robots.txt: 1 disallowed entry |/ |_http-server-header: Apache/2.2.14 (Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1 | http-title: Damn Vulnerable Web App (DVWA) - Login |_Requested resource was login.php 443/tcp open ssl/http Apache httpd 2.2.14 ((Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1) | http-cookie-flags: | /: | PHPSESSID: | httponly flag not set | http-robots.txt: 1 disallowed entry |/ |_http-server-header: Apache/2.2.14 (Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1 | http-title: Damn Vulnerable Web App (DVWA) - Login |_Requested resource was login.php | ssl-cert: Subject: commonName=localhost/organizationName=Apache Friends/stateOrProvinceName=Berlin/countryName=DE | Not valid before: 2004-10-01T09:10:30 |_Not valid after: 2010-09-30T09:10:30 |_ssl-date: 2019-03-26T07:34:27+00:00; +34s from scanner time. | sslv2: | SSLv2 supported | ciphers: | SSL2_RC2_128_CBC_WITH_MD5 | SSL2_RC2_128_CBC_EXPORT40_WITH_MD5 | SSL2_DES_192_EDE3_CBC_WITH_MD5 | SSL2_RC4_128_EXPORT40_WITH_MD5 | SSL2_IDEA_128_CBC_WITH_MD5 | SSL2_DES_64_CBC_WITH_MD5 | SSL2_RC4_128_WITH_MD5 3306/tcp open mysql MySQL (unauthorized) MAC Address: 00:0C:29:33:5D:C2 (VMware) Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.17 - 2.6.36 Network Distance: 1 hop Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: 33s, deviation: 0s, median: 33s TRACEROUTE HOP RTT ADDRESS 1 1.10 ms dvwa (192.168.1.105) OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done at Tue Mar 26 03:33:54 2019 -- 1 IP address (1 host up) scanned in 20.07 seconds
- La salida anterior muestra un análisis detallado del escaneo de nmap que se puede utilizar en otras actividades de hacking
Escaneo UDP
- Escriba portscan UDP-STANDARD 192.168.1.105
- UDP-STANDARD busca los puertos comunes de nmap e intenta encontrar servicios abiertos/cerrados
[goscan] > portscan UDP-STANDARD 192.168.1.105 [] Starting UDP port scan (common ports) [goscan] > [-] Executing command: nmap -Pn -sU -sC -A -T4 -p19,53,69,79,111,123,135,137,138,161,177,445,500,514,520,1434,1900,5353 192.168.1.105 -oA /root/.goscan/192.168.1.105/portscan/udp_standard_192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105
- Después de ejecutar la consulta anterior, se muestra cómo nmap utiliza diferentes consultas para buscar puertos abiertos. Después de que las exploraciones hayan completado el tipo, muestre los puertos para listar los puertos abiertos de la dirección IP
[goscan] > show ports +----------------+----------+---------------+---------------------------------------+ | HOST | PORT | STATUS | SERVICE | +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 19/udp | open|filtered | chargen +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 53/udp | closed | domain +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 69/udp | closed | tftp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 79/udp | open|filtered | finger +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 111/udp | closed | rpcbind +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 123/udp | open|filtered | ntp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 135/udp | closed | msrpc +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 137/udp | closed | netbios-ns +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 138/udp | closed | netbios-dgm +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 161/udp | closed | snmp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 177/udp | closed | xdmcp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 445/udp | closed | microsoft-ds +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 500/udp | closed | isakmp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 514/udp | open|filtered | syslog +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 520/udp | closed | route +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 1434/udp | open|filtered | ms-sql-m +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 1900/udp | open|filtered | upnp +----------------+----------+---------------+----------------------------------------+ | 192.168.1.105 | 5353/udp | closed | zeroconf +----------------+----------+---------------+----------------------------------------+
- Arriba se muestran los puertos abiertos del objetivo. Los anteriores son los puertos más comunes que se utilizan durante la exploración
- Goscan también guarda la salida al crear un directorio de direcciones IP escaneadas. Para acceder al tipo de directoriocd/root/.goscan
- Escriba cd 192.168.1.105
- Escriba ls & cat udp_full_192.168.1.105.nmap
root@kali:~/.goscan/192.168.1.105/portscan# cat udp_standard_192.168.1.105.nmap Nmap 7.70 scan initiated Tue Mar 26 04:05:25 2019 as: nmap -Pn -sU -sC -A -T4 -p19,53,69,79,111,123,135,137,138,161,177,445,500,514,520,1434,1900,5353 -oA /root/.goscan/192.168.1.105/portscan/udp_standard_192.168.1.105 192.168.1.105 Nmap scan report for dvwa (192.168.1.105) Host is up (0.00089s latency). PORT STATE SERVICE VERSION 19/udp open|filtered chargen 53/udp closed domain 69/udp closed tftp 79/udp open|filtered finger 111/udp closed rpcbind 123/udp open|filtered ntp 135/udp closed msrpc 137/udp closed netbios-ns 138/udp closed netbios-dgm 161/udp closed snmp 177/udp closed xdmcp 445/udp closed microsoft-ds 500/udp closed isakmp 514/udp open|filtered syslog 520/udp closed route 1434/udp open|filtered ms-sql-m 1900/udp open|filtered upnp 5353/udp closed zeroconf MAC Address: 00:0C:29:33:5D:C2 (VMware) Too many fingerprints match this host to give specific OS details Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 0.89 ms dvwa (192.168.1.105) OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done at Tue Mar 26 04:06:41 2019 -- 1 IP address (1 host up) scanned in 75.85 seconds
- La salida anterior muestra un análisis detallado del escaneo de nmap que se puede utilizar en otras actividades de hacking
- La salida anterior también se puede acceder dentro del directorio de salida de goscan. Como se muestra arriba se puede acceder accediendo a cd./root/.goscan/192.168.105
- Escriba show hosts
[goscan] > show hosts +----------------+--------+---------------------------------------------+------+------------------------------------------------------------------+ | ADDRESS | STATUS | OS | INFO | PORTS | +----------------+--------+---------------------------------------------+------+------------------------------------------------------------------+ | 192.168.1.105 | up | Linux 2.6.17 - 2.6.36 | | * 21/tcp open : ftp [ProFTPD 1.3.2c] | | | | | | * 22/tcp open : ssh [OpenSSH 5.3p1 Debian 3ubuntu4] | | | | | | * 80/tcp open : http [Apache httpd 2.2.14] | | | | | | * 443/tcp open : http [Apache httpd 2.2.14] | | | | | | * 3306/tcp open : mysql [MySQL ] | | | | | | * 19/udp open|filtered: chargen | | | | | | * 53/udp closed : domain | | | | | | * 69/udp closed : tftp | | | | | | * 79/udp open|filtered: finger | | | | | | * 111/udp closed : rpcbind | | | | | | * 123/udp open|filtered: ntp | | | | | | * 135/udp closed : msrpc | | | | | | * 137/udp closed : netbios-ns | | | | | | * 138/udp closed : netbios-dgm | | | | | | * 161/udp closed : snmp | | | | | | * 177/udp closed : xdmcp | | | | | | * 445/udp closed : microsoft-ds | | | | | | * 500/udp closed : isakmp | | | | | | * 514/udp open|filtered: syslog | | | | | | * 520/udp closed : route | | | | | | * 1434/udp open|filtered: ms-sql-m | | | | | | * 1900/udp open|filtered: upnp | | | | | | * 5353/udp closed : zeroconf | | | | | | | +----------------+--------+---------------------------------------------+------+------------------------------------------------------------------+ | 162.241.216.11 | up | DD-WRT v23 (Linux 2.4.36) | | * 21/tcp open : ftp [Pure-FTPd ] | | | | | | * 22/tcp open : ssh [OpenSSH 5.3] | | | | | | * 25/tcp open : tcpwrapped | | | | | | * 26/tcp open : smtp [Exim smtpd 4.91] | | | | | | * 53/tcp open : domain [ISC BIND 9.8.2rc1] | | | | | | * 80/tcp open : http [nginx 1.14.1] | | | | | | * 110/tcp open : pop3 [Dovecot pop3d ] | | | | | | * 139/tcp filtered: netbios-ssn | | | | | | * 143/tcp open : imap [Dovecot imapd ] | | | | | | * 443/tcp open : http [nginx 1.14.1] | | | | | | * 445/tcp filtered: microsoft-ds | | | | | | * 465/tcp open : tcpwrapped | | | | | | * 587/tcp open : smtp [Exim smtpd 4.91] | | | | | | * 993/tcp open : imap [Dovecot imapd ] | | | | | | * 995/tcp open : pop3 [Dovecot pop3d ] | | | | | | * 1720/tcp filtered: h323q931 | | | | | | * 3306/tcp open : mysql [MySQL 5.6.41-84.1] | | | | | | * 5060/tcp filtered: sip | | | | | | * 5432/tcp open : postgresql [PostgreSQL DB ] | | | | | | * 8080/tcp open : http [nginx 1.14.1] | | | | | | * 8443/tcp open : http [nginx 1.14.1] | | | | | | | +----------------+--------+---------------------------------------------+------+------------------------------------------------------------------+
- La consulta anterior muestra los hosts que se escanean y también muestra los puertos que se encuentran utilizando el escáner nmap. Estas pruebas se pueden utilizar para piratear dispositivos IoT
Enumerar
- Esta consulta intentará enumerar los servicios detectados para apuntar
- Teclee enumerate ALL DRY 192.168.1.105
- ALL escaneará automáticamente los servicios abiertos
- FINGER: Este comando intenta encontrar información sobre los usuarios de computadoras.
- HTTP (Protocolo de transporte de hipertexto): este es el protocolo más común utilizado en toda la red. Este protocolo se utiliza para comunicarse con navegadores web y servidores web.
- FTP (Protocolo de transporte de archivos): este protocolo se utiliza para transferir archivos entre el cliente y los servidores.
- SMB (bloque de mensajes de servicio): características de Windows que permiten compartir archivos de forma remota a través de la misma red.
- RDP (Protocolo de escritorio remoto): este protocolo se utiliza para transmitir pantallas de la plataforma basada en Windows
- DRY solo mostrará los comandos y no enumerará el uso de esos comandos
[goscan] > enumerate ALL DRY 192.168.1.105 [] Starting service enumeration [goscan] > [] Starting Enumeration: 192.168.1.105:21 (ftp) [-] To be run: nmap -sV -Pn --script=ftp-anon,ftp-bounce,ftp-libopie,ftp-proftpd-backdoor,ftp-vsftpd-backdoor,ftp-vuln-cve2010-4221 -p21 192.168.1.105 -oA /root/.goscan/192.168.1.105/FTP/192.168.1.105_ftp_nmap_21 [-] Created directory: /root/.goscan/192.168.1.105/FTP [-] [DRY RUN] ftp-user-enum.pl -U /usr/share/wfuzz/wordlist/fuzzdb/wordlists-user-passwd/names/namelist.txt -t 192.168.1.105 > /root/.goscan/192.168.1.105/FTP/192.168.1.105_ftp_user-enum [-] [DRY RUN] hydra -L /usr/share/wfuzz/wordlist/fuzzdb/wordlists-user-passwd/names/namelist.txt -P /usr/share/wordlists/metasploit/unix_passwords.txt -f -o /root/.goscan/192.168.1.105/FTP/192.168.1.105_ftp_hydra -u 192.168.1.105 -s 21 ftp [] Starting Enumeration: 192.168.1.105:80 (http) [-] To be run: nmap -sV -Pn --script=http-vhosts,http-userdir-enum,http-apache-negotiation,http-backup-finder,http-config-backup,http-default-accounts,http-methods,http-method-tamper,http-passwd,http-sitemap-generator,http-auth-finder,http-auth,http-fileupload-exploiter,http-put,http-sql-injection,http-stored-xss,http-xssed,http-php-version,http-unsafe-output-escaping,http-phpmyadmin-dir-traversal,http-ntlm-info,http-phpself-xss,http-open-redirect,http-iis-webdav-vuln,http-form-fuzzer,http-vuln-cve2009-3960,http-vuln-cve2010-0738,http-vuln-cve2010-2861,http-vuln-cve2011-3368,http-vuln-cve2012-1823,http-vuln-cve2013-0156,http-robots.txt,http-wordpress-brute,http-wordpress-enum --script-args http-put.url='/uploads/rootme.php',http-put.file='/root/www/php-reverse.php',basepath='/' -p80 192.168.1.105 -oA /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_nmap [-] [DRY RUN] nikto -host 192.168.1.105 -p 80 > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_nikto [-] [DRY RUN] dirb http://192.168.1.105:80 -o /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_dirb -S -r [-] [DRY RUN] sqlmap -u http://192.168.1.105:80 --crawl=1 > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_sqlmap [-] [DRY RUN] fimap -u "http://192.168.1.105:80" > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_fimap [] Starting Enumeration: 192.168.1.105:443 (http) [-] To be run: nmap -sV -Pn --script=http-vhosts,http-userdir-enum,http-apache-negotiation,http-backup-finder,http-config-backup,http-default-accounts,http-methods,http-method-tamper,http-passwd,http-sitemap-generator,http-auth-finder,http-auth,http-fileupload-exploiter,http-put,http-sql-injection,http-stored-xss,http-xssed,http-php-version,http-unsafe-output-escaping,http-phpmyadmin-dir-traversal,http-ntlm-info,http-phpself-xss,http-open-redirect,http-iis-webdav-vuln,http-form-fuzzer,http-vuln-cve2009-3960,http-vuln-cve2010-0738,http-vuln-cve2010-2861,http-vuln-cve2011-3368,http-vuln-cve2012-1823,http-vuln-cve2013-0156,http-robots.txt,http-wordpress-brute,http-wordpress-enum --script-args http-put.url='/uploads/rootme.php',http-put.file='/root/www/php-reverse.php',basepath='/' -p443 192.168.1.105 -oA /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_nmap [-] [DRY RUN] nikto -host 192.168.1.105 -p 443 > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_nikto [-] [DRY RUN] dirb http://192.168.1.105:443 -o /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_dirb -S -r [-] [DRY RUN] sqlmap -u http://192.168.1.105:443 --crawl=1 > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_sqlmap [-] [DRY RUN] fimap -u "http://192.168.1.105:443" > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_fimap [] Starting Enumeration: 192.168.1.105:3306 (mysql) [-] To be run: nmap -sV -Pn --script=mysql-brute,mysql-databases,mysql-empty-password,mysql-enum,mysql-info,mysql-users,mysql-variables,mysql-vuln-cve2012-2122 -p3306 192.168.1.105 -oA /root/.goscan/192.168.1.105/SQL/192.168.1.105_sql_mysql_nmap_3306 [] Starting Enumeration: 192.168.1.105:22 (ssh) [-] Created directory: /root/.goscan/192.168.1.105/SSH [-] [DRY RUN] hydra -L /usr/share/wfuzz/wordlist/fuzzdb/wordlists-user-passwd/names/namelist.txt -P /usr/share/wordlists/metasploit/unix_passwords.txt -f -o /root/.goscan/192.168.1.105/SSH/192.168.1.105_ssh_hydra -u 192.168.1.105 -s 22 ssh [+] [ALL] Enumeration finished on host: 192.168.1.105 [+] [ALL] Output has been saved at: /root/.goscan
- La consulta anterior muestra que el comando se puede ejecutar en las direcciones IP de destino. La salida anterior muestra que nikto, sqlmap, hydra & fimap se pueden usar para enumerar más el objetivo
- Un análisis más detallado de la herramienta muestra que goscan consume tiempo y utiliza peajes de código abierto en el backend
AUTOMATE YOUR INITIAL PHASE OF PENTESTING

ORIGINAL CONTENT: https://www.securitynewspaper.com/2019/03/26/automate-your-initial-phase-of-pentesting/
Different automation & manual tools/ techniques are used in pentesting. Considering on the target web application scenario scanning is performed. Security researchers/ pentesters always tries to found the vulnerability in source code or ports which are vulnerable. Ethical hackingresearcher, Delhi India of International Institute of Cyber Security, recently demonstrated a critical vulnerability using a very basic tool called goscan, which we will talk about in next sections.
GOscan is an network scanner which provides automation over network scanning. This tool is used to find open ports & services on the target. It supports all main features of enumeration. It uses SQLite databases while scanning. According to ethical hacking researchers of international institute of cyber security Goscan tool can be considered in different phases of pentesting.
- On attacker side Goscan has been tested on Kali Linux 2018.4 amd64. And for target we have used DVWA.
- Download DVWA iso from : http://www.dvwa.co.uk/DVWA-1.0.7.iso
- Open DVWA-1.0.7.iso in vmware. Open Vmware click on open. Go to location where you have downloaded DVWA iso. Select that iso & open in Vmware.
- Click on Power on the virtual machine. Type ifconfig to know IP address Open browser type DVWA ip address.
- By default DVWA username : admin & password : password
- And your DVWA has now setup. After configuring target, now setup goscan.
- This tool build on GO environment. If GO is not installed. Download & configure GO before using GOSCAN.
- For downloading GO type
wget https://dl.google.com/go/go1.12.1.linux-amd64.tar.gz
root@kali:/home/iicybersecurity# wget https://dl.google.com/go/go1.12.1.linux-amd64.tar.gz --2019-03-18 02:21:59-- https://dl.google.com/go/go1.12.1.linux-amd64.tar.gz Resolving dl.google.com (dl.google.com)… 172.217.167.14, 2404:6800:4002:80a::200e Connecting to dl.google.com (dl.google.com)|172.217.167.14|:443… connected. HTTP request sent, awaiting response… 200 OK Length: 127906702 (122M) [application/octet-stream] Saving to: ‘go1.12.1.linux-amd64.tar.gz’ go1.12.1.linux-amd64.tar.gz 100%[===========================================================>] 121.98M 1.89MB/s in 93s 2019-03-19 12:48:43 (1.31 MB/s) - ‘go1.12.1.linux-amd64.tar.gz’ saved [127906702/127906702]
- Type tar -xvzf go1.12.1.linux-amd64.tar.gz
- Type cd go & cd bin
- Copy the go file type cp go /usr/local/bin/go
- Type export GOROOT=/home/iicybersecurity/go/bin
- Type echo $GOROOT
root@kali:/home/iicybersecurity/Downloads# export GOROOT=/home/iicyberseurity/go/bin root@kali:/home/iicybersecurity/Downloads# echo $GOROOT /home/iicyebrsecurity/go/bin
- After installing type wget https://github.com/marco-lancini/goscan/releases/download/v2.4/goscan_2.4_linux_amd64.zip
- Type unzip goscan_2.4_linux_amd64.zip
- Type chmod u+x goscan
- Type ./goscan
root@kali:/home/iicybersecurity/Downloads# ./goscan
__ ____/_______ ___/_ ____/__ |__ | / /
_ / __ _ __ \____ \_ / __ /| |_ |/ /
/ /_/ / / /_/ /___/ // /___ _ ___ | /| /
\____/ \____//____/ \____/ /_/ |_/_/ |_/
goscan (v.2.4)
Marco Lancini [@LanciniMarco]
- Before running an scan, add target IP address in goscan database. Type load target SINGLE 192.168.1.105
- You can also add multiple IP addresses into goscan database. Type load target MULTIPLE /home/iicybersecurity/Downloads/Iplist.txt & select the txt containing IP addresses.
- Type show targets to check for the added IP addresses.
[goscan] > load target SINGLE 192.168.1.9 [*] Imported target: 192.168.1.9 [goscan] > show targets +---------------+------------+ | ADDRESS | STEP | +---------------+------------+ | 192.168.1.105 | IMPORTED | +---------------+------------+
- Before finding any services or ports on the target IP addresses. GOSCAN needs to ping on the added IP address.
- Every pentesting is initialized with PING (Packet Internet Groper) is most common utility which is used to check the availability on the internet. So goscan also checks with ping. For checking type sweep PING 192.168.1.105
[goscan] > sweep PING 192.168.1.105 [] Starting Ping Sweep [goscan] > [-] Created directory: /root/.goscan/192.168.1.105/sweep [-] Executing command: nmap -n -sn -PE -PP 192.168.1.105 -oA /root/.goscan/192.168.1.105/sweep/ping_192.168.1.105 [] [ping] Nmap work in progress on host: 192.168.1.105 [+] [ping] Nmap finished on host: 192.168.1.105 [+] [ping] Output has been saved at: /root/.goscan
- Type show targets to check for the available targets.
[goscan] > show targets +------------------+----------+ | ADDRESS | STEP | +------------------+----------+ | 192.168.1.105 | SWEEPED | +------------------+----------+
TCP SCAN :-
- Type portscan TCP-FULL 192.168.1.105
- portscan will find open ports of the target.
- goscan offers TCP & UDP scan. We have used TCP-FULL scan in which goscan will use most common network protocols.
- Goscan will scan for
- TCP-STANDARD : scan for top 200 TCP-SCAN
- TCP-PROD : scan for T3 RMI (Remote Method Invocation) protocol which is used for transforming information between weblogic & other programs
- TCP-VULN SCAN : scan for CVE listed nse scripts & tries to found vulnerabilities in IP address
- Then write target IP address 192.168.1.105
[goscan] > portscan TCP-FULL 192.168.1.105 [] Starting full TCP port scan [goscan] > [-] Executing command: nmap -Pn -sT -sC -A -T4 -p- 192.168.1.105 -oA /root/.goscan/192.168.1.105/portscan/tcp_full_192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [+] [tcp_standard] Nmap finished on host: 192.168.1.105 [+] [tcp_standard] Output has been saved at: /root/.goscan [+] [tcp_standard] Nmap finished on host: 192.168.1.105 [+] [tcp_standard] Output has been saved at: /root/.goscan
- After executing the above query it shows, how nmap uses different queries to scan for open ports. After scans has complete type show ports to list open ports of IP address.
[goscan] > show ports +----------------+----------+----------+---------------------------------------------+ | HOST | PORT | STATUS | SERVICE | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 21/tcp | open | ftp [ProFTPD 1.3.2c] [Unix] | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 22/tcp | open | ssh [OpenSSH 5.3p1 Debian 3ubuntu4] [Linux] | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 80/tcp | open | http [Apache httpd 2.2.14] | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 443/tcp | open | http [Apache httpd 2.2.14] | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 3306/tcp | open | mysql [MySQL ] | +----------------+----------+----------+---------------------------------------------+
- Above shows open ports of the target. The above are most common ports which are used while scanning.
- Goscan also saves the output by creating an directory of scanned IP address. For accessing the directory type cd /root/.goscan
- Type cd 192.168.1.105
- Type ls & cat tcp_full_192.168.1.105.nmap
root@kali:~/.goscan/192.168.1.105/portscan# ls tcp_full_192.168.1.105.nmap root@kali:~/.goscan/192.168.1.105/portscan# cat tcp_full_192.168.1.105.nmap Nmap 7.70 scan initiated Tue Mar 26 03:33:34 2019 as: nmap -Pn -sT -sC -A -T4 -p- -oA /root/.goscan/192.168.1.105/portscan/tcp_full_192.168.1.105 192.168.1.105 Nmap scan report for dvwa (192.168.1.105) Host is up (0.0011s latency). Not shown: 65530 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp ProFTPD 1.3.2c 22/tcp open ssh OpenSSH 5.3p1 Debian 3ubuntu4 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.2.14 ((Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1) | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set | http-robots.txt: 1 disallowed entry |/ |_http-server-header: Apache/2.2.14 (Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1 | http-title: Damn Vulnerable Web App (DVWA) - Login |_Requested resource was login.php 443/tcp open ssl/http Apache httpd 2.2.14 ((Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1) | http-cookie-flags: | /: | PHPSESSID: | httponly flag not set | http-robots.txt: 1 disallowed entry |/ |_http-server-header: Apache/2.2.14 (Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1 | http-title: Damn Vulnerable Web App (DVWA) - Login |_Requested resource was login.php | ssl-cert: Subject: commonName=localhost/organizationName=Apache Friends/stateOrProvinceName=Berlin/countryName=DE | Not valid before: 2004-10-01T09:10:30 |_Not valid after: 2010-09-30T09:10:30 |_ssl-date: 2019-03-26T07:34:27+00:00; +34s from scanner time. | sslv2: | SSLv2 supported | ciphers: | SSL2_RC2_128_CBC_WITH_MD5 | SSL2_RC2_128_CBC_EXPORT40_WITH_MD5 | SSL2_DES_192_EDE3_CBC_WITH_MD5 | SSL2_RC4_128_EXPORT40_WITH_MD5 | SSL2_IDEA_128_CBC_WITH_MD5 | SSL2_DES_64_CBC_WITH_MD5 | SSL2_RC4_128_WITH_MD5 3306/tcp open mysql MySQL (unauthorized) MAC Address: 00:0C:29:33:5D:C2 (VMware) Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.17 - 2.6.36 Network Distance: 1 hop Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: 33s, deviation: 0s, median: 33s TRACEROUTE HOP RTT ADDRESS 1 1.10 ms dvwa (192.168.1.105) OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done at Tue Mar 26 03:33:54 2019 -- 1 IP address (1 host up) scanned in 20.07 seconds
- The above output show detailed analysis of nmap scan which can be used in further hacking activities.
UDP SCAN :-
- Type portscan UDP-STANDARD 192.168.1.105
- UDP-STANDARD scans for the common ports of nmap & tries to find open/ closed services.
[goscan] > portscan UDP-STANDARD 192.168.1.105 [] Starting UDP port scan (common ports) [goscan] > [-] Executing command: nmap -Pn -sU -sC -A -T4 -p19,53,69,79,111,123,135,137,138,161,177,445,500,514,520,1434,1900,5353 192.168.1.105 -oA /root/.goscan/192.168.1.105/portscan/udp_standard_192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105
- After executing the above query it shows, how nmap uses different queries to scan for open ports. After scans has complete type show ports to list open ports of IP address.
[goscan] > show ports +----------------+----------+---------------+---------------------------------------+ | HOST | PORT | STATUS | SERVICE | +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 19/udp | open|filtered | chargen +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 53/udp | closed | domain +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 69/udp | closed | tftp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 79/udp | open|filtered | finger +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 111/udp | closed | rpcbind +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 123/udp | open|filtered | ntp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 135/udp | closed | msrpc +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 137/udp | closed | netbios-ns +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 138/udp | closed | netbios-dgm +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 161/udp | closed | snmp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 177/udp | closed | xdmcp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 445/udp | closed | microsoft-ds +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 500/udp | closed | isakmp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 514/udp | open|filtered | syslog +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 520/udp | closed | route +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 1434/udp | open|filtered | ms-sql-m +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 1900/udp | open|filtered | upnp +----------------+----------+---------------+----------------------------------------+ | 192.168.1.105 | 5353/udp | closed | zeroconf +----------------+----------+---------------+----------------------------------------+
- Above shows open ports of the target. The above are most common ports which are used while scanning.
- Goscan also saves the output by creating an directory of scanned IP address. For accessing the directory type cd /root/.goscan
- Type cd 192.168.1.105
- Type ls & cat udp_full_192.168.1.105.nmap
root@kali:~/.goscan/192.168.1.105/portscan# cat udp_standard_192.168.1.105.nmap Nmap 7.70 scan initiated Tue Mar 26 04:05:25 2019 as: nmap -Pn -sU -sC -A -T4 -p19,53,69,79,111,123,135,137,138,161,177,445,500,514,520,1434,1900,5353 -oA /root/.goscan/192.168.1.105/portscan/udp_standard_192.168.1.105 192.168.1.105 Nmap scan report for dvwa (192.168.1.105) Host is up (0.00089s latency). PORT STATE SERVICE VERSION 19/udp open|filtered chargen 53/udp closed domain 69/udp closed tftp 79/udp open|filtered finger 111/udp closed rpcbind 123/udp open|filtered ntp 135/udp closed msrpc 137/udp closed netbios-ns 138/udp closed netbios-dgm 161/udp closed snmp 177/udp closed xdmcp 445/udp closed microsoft-ds 500/udp closed isakmp 514/udp open|filtered syslog 520/udp closed route 1434/udp open|filtered ms-sql-m 1900/udp open|filtered upnp 5353/udp closed zeroconf MAC Address: 00:0C:29:33:5D:C2 (VMware) Too many fingerprints match this host to give specific OS details Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 0.89 ms dvwa (192.168.1.105) OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done at Tue Mar 26 04:06:41 2019 -- 1 IP address (1 host up) scanned in 75.85 seconds
- The above output show detailed analysis of nmap scan which can be used in further hacking activities.
- The above output can also be accesse inside goscan output directory. As shown above it can be accessed by going to cd
/root/.goscan/192.168.105 - Type show hosts
[goscan] > show hosts +----------------+--------+---------------------------------------------+------+------------------------------------------------------------------+ | ADDRESS | STATUS | OS | INFO | PORTS | +----------------+--------+---------------------------------------------+------+------------------------------------------------------------------+ | 192.168.1.105 | up | Linux 2.6.17 - 2.6.36 | | * 21/tcp open : ftp [ProFTPD 1.3.2c] | | | | | | * 22/tcp open : ssh [OpenSSH 5.3p1 Debian 3ubuntu4] | | | | | | * 80/tcp open : http [Apache httpd 2.2.14] | | | | | | * 443/tcp open : http [Apache httpd 2.2.14] | | | | | | * 3306/tcp open : mysql [MySQL ] | | | | | | * 19/udp open|filtered: chargen | | | | | | * 53/udp closed : domain | | | | | | * 69/udp closed : tftp | | | | | | * 79/udp open|filtered: finger | | | | | | * 111/udp closed : rpcbind | | | | | | * 123/udp open|filtered: ntp | | | | | | * 135/udp closed : msrpc | | | | | | * 137/udp closed : netbios-ns | | | | | | * 138/udp closed : netbios-dgm | | | | | | * 161/udp closed : snmp | | | | | | * 177/udp closed : xdmcp | | | | | | * 445/udp closed : microsoft-ds | | | | | | * 500/udp closed : isakmp | | | | | | * 514/udp open|filtered: syslog | | | | | | * 520/udp closed : route | | | | | | * 1434/udp open|filtered: ms-sql-m | | | | | | * 1900/udp open|filtered: upnp | | | | | | * 5353/udp closed : zeroconf | | | | | | | +----------------+--------+---------------------------------------------+------+------------------------------------------------------------------+ | 162.241.216.11 | up | DD-WRT v23 (Linux 2.4.36) | | * 21/tcp open : ftp [Pure-FTPd ] | | | | | | * 22/tcp open : ssh [OpenSSH 5.3] | | | | | | * 25/tcp open : tcpwrapped | | | | | | * 26/tcp open : smtp [Exim smtpd 4.91] | | | | | | * 53/tcp open : domain [ISC BIND 9.8.2rc1] | | | | | | * 80/tcp open : http [nginx 1.14.1] | | | | | | * 110/tcp open : pop3 [Dovecot pop3d ] | | | | | | * 139/tcp filtered: netbios-ssn | | | | | | * 143/tcp open : imap [Dovecot imapd ] | | | | | | * 443/tcp open : http [nginx 1.14.1] | | | | | | * 445/tcp filtered: microsoft-ds | | | | | | * 465/tcp open : tcpwrapped | | | | | | * 587/tcp open : smtp [Exim smtpd 4.91] | | | | | | * 993/tcp open : imap [Dovecot imapd ] | | | | | | * 995/tcp open : pop3 [Dovecot pop3d ] | | | | | | * 1720/tcp filtered: h323q931 | | | | | | * 3306/tcp open : mysql [MySQL 5.6.41-84.1] | | | | | | * 5060/tcp filtered: sip | | | | | | * 5432/tcp open : postgresql [PostgreSQL DB ] | | | | | | * 8080/tcp open : http [nginx 1.14.1] | | | | | | * 8443/tcp open : http [nginx 1.14.1] | | | | | | | +----------------+--------+---------------------------------------------+------+------------------------------------------------------------------+
- The above query shows the hosts which are scanned & also shows ports which are found using nmap scanner. These tests can be used to do hacking on IoT devices.
ENUMERATE :-
- This query will try to enumerate detected services to target.
- Type enumerate ALL DRY 192.168.1.105
- ALL will automatically scan open services.
- FINGER : This command tries to find information about computer users.
- HTTP (Hyper Text Transport Protocol) : This is most common protocol used on the entire network. This protocol is used to communicate with web browsers & web servers.
- FTP (File Transport Protocol) : This protocol is used to transfer files between client & the servers.
- SMB (Service Message Block) : An Windows features which allows to share files remotely over the same network.
- RDP (Remote Desktop Protocol) : This protocol is used to transmits screens of Windows Based platform.
- Dry will only show commands & will not enumerate using those commands.
[goscan] > enumerate ALL DRY 192.168.1.105 [] Starting service enumeration [goscan] > [] Starting Enumeration: 192.168.1.105:21 (ftp) [-] To be run: nmap -sV -Pn --script=ftp-anon,ftp-bounce,ftp-libopie,ftp-proftpd-backdoor,ftp-vsftpd-backdoor,ftp-vuln-cve2010-4221 -p21 192.168.1.105 -oA /root/.goscan/192.168.1.105/FTP/192.168.1.105_ftp_nmap_21 [-] Created directory: /root/.goscan/192.168.1.105/FTP [-] [DRY RUN] ftp-user-enum.pl -U /usr/share/wfuzz/wordlist/fuzzdb/wordlists-user-passwd/names/namelist.txt -t 192.168.1.105 > /root/.goscan/192.168.1.105/FTP/192.168.1.105_ftp_user-enum [-] [DRY RUN] hydra -L /usr/share/wfuzz/wordlist/fuzzdb/wordlists-user-passwd/names/namelist.txt -P /usr/share/wordlists/metasploit/unix_passwords.txt -f -o /root/.goscan/192.168.1.105/FTP/192.168.1.105_ftp_hydra -u 192.168.1.105 -s 21 ftp [] Starting Enumeration: 192.168.1.105:80 (http) [-] To be run: nmap -sV -Pn --script=http-vhosts,http-userdir-enum,http-apache-negotiation,http-backup-finder,http-config-backup,http-default-accounts,http-methods,http-method-tamper,http-passwd,http-sitemap-generator,http-auth-finder,http-auth,http-fileupload-exploiter,http-put,http-sql-injection,http-stored-xss,http-xssed,http-php-version,http-unsafe-output-escaping,http-phpmyadmin-dir-traversal,http-ntlm-info,http-phpself-xss,http-open-redirect,http-iis-webdav-vuln,http-form-fuzzer,http-vuln-cve2009-3960,http-vuln-cve2010-0738,http-vuln-cve2010-2861,http-vuln-cve2011-3368,http-vuln-cve2012-1823,http-vuln-cve2013-0156,http-robots.txt,http-wordpress-brute,http-wordpress-enum --script-args http-put.url='/uploads/rootme.php',http-put.file='/root/www/php-reverse.php',basepath='/' -p80 192.168.1.105 -oA /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_nmap [-] [DRY RUN] nikto -host 192.168.1.105 -p 80 > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_nikto [-] [DRY RUN] dirb http://192.168.1.105:80 -o /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_dirb -S -r [-] [DRY RUN] sqlmap -u http://192.168.1.105:80 --crawl=1 > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_sqlmap [-] [DRY RUN] fimap -u "http://192.168.1.105:80" > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_fimap [] Starting Enumeration: 192.168.1.105:443 (http) [-] To be run: nmap -sV -Pn --script=http-vhosts,http-userdir-enum,http-apache-negotiation,http-backup-finder,http-config-backup,http-default-accounts,http-methods,http-method-tamper,http-passwd,http-sitemap-generator,http-auth-finder,http-auth,http-fileupload-exploiter,http-put,http-sql-injection,http-stored-xss,http-xssed,http-php-version,http-unsafe-output-escaping,http-phpmyadmin-dir-traversal,http-ntlm-info,http-phpself-xss,http-open-redirect,http-iis-webdav-vuln,http-form-fuzzer,http-vuln-cve2009-3960,http-vuln-cve2010-0738,http-vuln-cve2010-2861,http-vuln-cve2011-3368,http-vuln-cve2012-1823,http-vuln-cve2013-0156,http-robots.txt,http-wordpress-brute,http-wordpress-enum --script-args http-put.url='/uploads/rootme.php',http-put.file='/root/www/php-reverse.php',basepath='/' -p443 192.168.1.105 -oA /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_nmap [-] [DRY RUN] nikto -host 192.168.1.105 -p 443 > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_nikto [-] [DRY RUN] dirb http://192.168.1.105:443 -o /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_dirb -S -r [-] [DRY RUN] sqlmap -u http://192.168.1.105:443 --crawl=1 > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_sqlmap [-] [DRY RUN] fimap -u "http://192.168.1.105:443" > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_fimap [] Starting Enumeration: 192.168.1.105:3306 (mysql) [-] To be run: nmap -sV -Pn --script=mysql-brute,mysql-databases,mysql-empty-password,mysql-enum,mysql-info,mysql-users,mysql-variables,mysql-vuln-cve2012-2122 -p3306 192.168.1.105 -oA /root/.goscan/192.168.1.105/SQL/192.168.1.105_sql_mysql_nmap_3306 [] Starting Enumeration: 192.168.1.105:22 (ssh) [-] Created directory: /root/.goscan/192.168.1.105/SSH [-] [DRY RUN] hydra -L /usr/share/wfuzz/wordlist/fuzzdb/wordlists-user-passwd/names/namelist.txt -P /usr/share/wordlists/metasploit/unix_passwords.txt -f -o /root/.goscan/192.168.1.105/SSH/192.168.1.105_ssh_hydra -u 192.168.1.105 -s 22 ssh [+] [ALL] Enumeration finished on host: 192.168.1.105 [+] [ALL] Output has been saved at: /root/.goscan
- The above query shows that what command can be executed on the target IP addresses. The above output shows that nikto, sqlmap, hydra & fimap can be used to further enumerate the target.
- Further analyze of the tool shows that goscan consumes time and it uses open source tolls in the backend.
CÓMO AUTOMATIZAR LA FASE INICIAL DE PENTESTING

CONTENIDO ORIGINAL: https://noticiasseguridad.com/tutoriales/como-automatizar-la-fase-inicial-de-pentesting/
En el pentesting se utilizan diferentes técnicas manuales y automáticas según la aplicación web que se esté analizando. Los pentesters tratarán de encontrar las vulnerabilidades de seguridad en el código fuente o en los puertos vulnerables. Investigadores en hacking ético del Instituto Internacional de Seguridad Cibernética (IICS) demostraron recientemente una vulnerabilidad crítica gracias a una herramienta llamada GOscan, misma que presentaremos a continuación.
GOscan es un escáner de red que proporciona automatización durante este procedimiento. Esta herramienta se usa para encontrar puertos y servicios abiertos en el objetivo de nuestras pruebas. GOscan es compatible con todas las características principales de enumeración. Esta herramienta usa bases de datos SQLite durante el escaneo.
Acorde a los investigadores en hacking ético del IICS, GOscan puede ser una herramienta funcional en distintas fases del pentesting.
- Del lado del atacante, Goscan ha sido probado en Kali Linux 2018.4 amd64. Y para el objetivo hemos utilizado DVWA
- Descargar DVWA desde http://www.dvwa.co.uk/DVWA-1.0.7.iso
- Abra DVWA-1.0.7.iso en vmware. Abrir Vmware haga clic en abrir. Ir a la ubicación donde ha descargado DVWA iso. Seleccione que iso & abrir en Vmware
- Haga clic en Encender en la máquina virtual. Escriba ifconfig para saber la dirección IP; abra el navegador y escriba DVWA ip address
- Por defecto el nombre de usuario DVWA: admin y contraseña: password
- DVWA ya está configurada. Después de configurar el objetivo, ahora configura GOscan
- Esta herramienta se basa en el entorno GO. Si GO no está instalado, descargue y configure GO antes de usar GOSCAN
- Para descargar GO, escriba: wget https://dl.google.com/go/go1.12.1.linux-amd64.tar.gz
root@kali:/home/iicybersecurity# wget https://dl.google.com/go/go1.12.1.linux-amd64.tar.gz --2019-03-18 02:21:59-- https://dl.google.com/go/go1.12.1.linux-amd64.tar.gz Resolving dl.google.com (dl.google.com)… 172.217.167.14, 2404:6800:4002:80a::200e Connecting to dl.google.com (dl.google.com)|172.217.167.14|:443… connected. HTTP request sent, awaiting response… 200 OK Length: 127906702 (122M) [application/octet-stream] Saving to: ‘go1.12.1.linux-amd64.tar.gz’ go1.12.1.linux-amd64.tar.gz 100%[===========================================================>] 121.98M 1.89MB/s in 93s 2019-03-19 12:48:43 (1.31 MB/s) - ‘go1.12.1.linux-amd64.tar.gz’ saved [127906702/127906702]
- Escriba tar -xvzf go1.12.1.linux-amd64.tar.gz
- Escriba cd go y cd bin
- Copie el tipo de archivo go cp go / usr / local / bin / go
- Escriba export GOROOT = / home / iicybersecurity / go / bin
- Escriba echo $ GOROOT
root@kali:/home/iicybersecurity/Downloads# export GOROOT=/home/iicyberseurity/go/bin root@kali:/home/iicybersecurity/Downloads# echo $GOROOT /home/iicyebrsecurity/go/bin
- Después de instalar teclee wget https://github.com/marco-lancini/goscan/releases/download/v2.4/goscan_2.4_linux_amd64.zip
- Escriba unzip goscan_2.4_linux_amd64.zip
- Escriba chmod u + x goscan
- Escriba ./goscan
root@kali:/home/iicybersecurity/Downloads# ./goscan
__ ____/_______ ___/_ ____/__ |__ | / /
_ / __ _ __ \____ \_ / __ /| |_ |/ /
/ /_/ / / /_/ /___/ // /___ _ ___ | /| /
\____/ \____//____/ \____/ /_/ |_/_/ |_/
goscan (v.2.4)
Marco Lancini [@LanciniMarco]
- Antes de ejecutar un análisis, agregue la dirección IP de destino en la base de datos de GOscan. Escriba load target SINGLE 192.168.1.105
- También puede agregar múltiples direcciones IP en la base de datos de goscan. Escriba load target MULTIPLE /home/iicybersecurity/Downloads/Iplist.txt y seleccione el txt que contiene las direcciones IP
- Escriba show targets para comprobar las direcciones IP agregadas
[goscan] > load target SINGLE 192.168.1.9 [*] Imported target: 192.168.1.9 [goscan] > show targets +---------------+------------+ | ADDRESS | STEP | +---------------+------------+ | 192.168.1.105 | IMPORTED | +---------------+------------+
- Antes de encontrar cualquier servicio o puerto en las direcciones IP de destino. GOSCAN necesita hacer ping en la dirección IP agregada
- Cada pentesting se inicializa con PING (Packet Internet Groper) es la utilidad más común que se utiliza para verificar la disponibilidad en Internet. Así que goscan también comprueba con ping. Para comprobar escriba sweep PING 192.168.1.105
[goscan] > sweep PING 192.168.1.105 [] Starting Ping Sweep [goscan] > [-] Created directory: /root/.goscan/192.168.1.105/sweep [-] Executing command: nmap -n -sn -PE -PP 192.168.1.105 -oA /root/.goscan/192.168.1.105/sweep/ping_192.168.1.105 [] [ping] Nmap work in progress on host: 192.168.1.105 [+] [ping] Nmap finished on host: 192.168.1.105 [+] [ping] Output has been saved at: /root/.goscan
- Escriba show targets para comprobar los objetivos disponibles
[goscan] > show targets +------------------+----------+ | ADDRESS | STEP | +------------------+----------+ | 192.168.1.105 | SWEEPED | +------------------+----------+
Escaneo TCP
- Escriba portscan TCP-FULL 192.168.1.105portscan encontrará puertos abiertos del destino. GOscan ofrece escaneo TCP y UDP
- Hemos utilizado TCP-FULL scan en el que goscan usará los protocolos de red más comunes
GOscan buscará:
- TCP-ESTÁNDAR: búsqueda de los mejores 200 TCP-SCAN
- TCP-PROD: escanea el protocolo T3 RMI (Invocación de método remoto) que se usa para transformar información entre weblogic y otros programas
- TCP-VULN SCAN: busca scripts nse enumerados en CVE e intenta encontrar vulnerabilidades en la dirección IP
- Luego escriba la dirección IP de destino 192.168.1.105
[goscan] > portscan TCP-FULL 192.168.1.105 [] Starting full TCP port scan [goscan] > [-] Executing command: nmap -Pn -sT -sC -A -T4 -p- 192.168.1.105 -oA /root/.goscan/192.168.1.105/portscan/tcp_full_192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [] [tcp_full] Nmap work in progress on host: 192.168.1.105 [+] [tcp_standard] Nmap finished on host: 192.168.1.105 [+] [tcp_standard] Output has been saved at: /root/.goscan [+] [tcp_standard] Nmap finished on host: 192.168.1.105 [+] [tcp_standard] Output has been saved at: /root/.goscan
- Después de ejecutar la consulta anterior, se muestra cómo nmap utiliza diferentes consultas para buscar puertos abiertos. Después de que las exploraciones hayan completado, escriba show ports para mostrar la lista de puertos abiertos en la dirección IP
[goscan] > show ports +----------------+----------+----------+---------------------------------------------+ | HOST | PORT | STATUS | SERVICE | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 21/tcp | open | ftp [ProFTPD 1.3.2c] [Unix] | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 22/tcp | open | ssh [OpenSSH 5.3p1 Debian 3ubuntu4] [Linux] | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 80/tcp | open | http [Apache httpd 2.2.14] | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 443/tcp | open | http [Apache httpd 2.2.14] | +----------------+----------+----------+---------------------------------------------+ | 192.168.1.105 | 3306/tcp | open | mysql [MySQL ] | +----------------+----------+----------+---------------------------------------------+
- Arriba se muestran los puertos abiertos del objetivo. Los anteriores son los puertos más comunes que se utilizan durante la exploración
- Goscan también guarda la salida al crear un directorio de direcciones IP escaneadas.
- Para acceder al directorio escriba cd /root/.goscan
- Escriba cd 192.168.1.105
- Escriba ls & cat tcp_full_192.168.1.105.nmap
root@kali:~/.goscan/192.168.1.105/portscan# ls tcp_full_192.168.1.105.nmap root@kali:~/.goscan/192.168.1.105/portscan# cat tcp_full_192.168.1.105.nmap Nmap 7.70 scan initiated Tue Mar 26 03:33:34 2019 as: nmap -Pn -sT -sC -A -T4 -p- -oA /root/.goscan/192.168.1.105/portscan/tcp_full_192.168.1.105 192.168.1.105 Nmap scan report for dvwa (192.168.1.105) Host is up (0.0011s latency). Not shown: 65530 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp ProFTPD 1.3.2c 22/tcp open ssh OpenSSH 5.3p1 Debian 3ubuntu4 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.2.14 ((Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1) | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set | http-robots.txt: 1 disallowed entry |/ |_http-server-header: Apache/2.2.14 (Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1 | http-title: Damn Vulnerable Web App (DVWA) - Login |_Requested resource was login.php 443/tcp open ssl/http Apache httpd 2.2.14 ((Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1) | http-cookie-flags: | /: | PHPSESSID: | httponly flag not set | http-robots.txt: 1 disallowed entry |/ |_http-server-header: Apache/2.2.14 (Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1 | http-title: Damn Vulnerable Web App (DVWA) - Login |_Requested resource was login.php | ssl-cert: Subject: commonName=localhost/organizationName=Apache Friends/stateOrProvinceName=Berlin/countryName=DE | Not valid before: 2004-10-01T09:10:30 |_Not valid after: 2010-09-30T09:10:30 |_ssl-date: 2019-03-26T07:34:27+00:00; +34s from scanner time. | sslv2: | SSLv2 supported | ciphers: | SSL2_RC2_128_CBC_WITH_MD5 | SSL2_RC2_128_CBC_EXPORT40_WITH_MD5 | SSL2_DES_192_EDE3_CBC_WITH_MD5 | SSL2_RC4_128_EXPORT40_WITH_MD5 | SSL2_IDEA_128_CBC_WITH_MD5 | SSL2_DES_64_CBC_WITH_MD5 | SSL2_RC4_128_WITH_MD5 3306/tcp open mysql MySQL (unauthorized) MAC Address: 00:0C:29:33:5D:C2 (VMware) Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.17 - 2.6.36 Network Distance: 1 hop Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: 33s, deviation: 0s, median: 33s TRACEROUTE HOP RTT ADDRESS 1 1.10 ms dvwa (192.168.1.105) OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done at Tue Mar 26 03:33:54 2019 -- 1 IP address (1 host up) scanned in 20.07 seconds
- La salida anterior muestra un análisis detallado del escaneo de nmap que se puede utilizar en otras actividades de hacking
Escaneo UDP
- Escriba portscan UDP-STANDARD 192.168.1.105
- UDP-STANDARD busca los puertos comunes de nmap e intenta encontrar servicios abiertos/cerrados
[goscan] > portscan UDP-STANDARD 192.168.1.105 [] Starting UDP port scan (common ports) [goscan] > [-] Executing command: nmap -Pn -sU -sC -A -T4 -p19,53,69,79,111,123,135,137,138,161,177,445,500,514,520,1434,1900,5353 192.168.1.105 -oA /root/.goscan/192.168.1.105/portscan/udp_standard_192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105 [] [udp_standard] Nmap work in progress on host: 192.168.1.105
- Después de ejecutar la consulta anterior, se muestra cómo nmap utiliza diferentes consultas para buscar puertos abiertos. Después de que las exploraciones hayan completado el tipo, muestre los puertos para listar los puertos abiertos de la dirección IP
[goscan] > show ports +----------------+----------+---------------+---------------------------------------+ | HOST | PORT | STATUS | SERVICE | +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 19/udp | open|filtered | chargen +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 53/udp | closed | domain +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 69/udp | closed | tftp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 79/udp | open|filtered | finger +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 111/udp | closed | rpcbind +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 123/udp | open|filtered | ntp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 135/udp | closed | msrpc +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 137/udp | closed | netbios-ns +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 138/udp | closed | netbios-dgm +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 161/udp | closed | snmp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 177/udp | closed | xdmcp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 445/udp | closed | microsoft-ds +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 500/udp | closed | isakmp +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 514/udp | open|filtered | syslog +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 520/udp | closed | route +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 1434/udp | open|filtered | ms-sql-m +----------------+----------+---------------+---------------------------------------+ | 192.168.1.105 | 1900/udp | open|filtered | upnp +----------------+----------+---------------+----------------------------------------+ | 192.168.1.105 | 5353/udp | closed | zeroconf +----------------+----------+---------------+----------------------------------------+
- Arriba se muestran los puertos abiertos del objetivo. Los anteriores son los puertos más comunes que se utilizan durante la exploración
- Goscan también guarda la salida al crear un directorio de direcciones IP escaneadas. Para acceder al tipo de directoriocd/root/.goscan
- Escriba cd 192.168.1.105
- Escriba ls & cat udp_full_192.168.1.105.nmap
root@kali:~/.goscan/192.168.1.105/portscan# cat udp_standard_192.168.1.105.nmap Nmap 7.70 scan initiated Tue Mar 26 04:05:25 2019 as: nmap -Pn -sU -sC -A -T4 -p19,53,69,79,111,123,135,137,138,161,177,445,500,514,520,1434,1900,5353 -oA /root/.goscan/192.168.1.105/portscan/udp_standard_192.168.1.105 192.168.1.105 Nmap scan report for dvwa (192.168.1.105) Host is up (0.00089s latency). PORT STATE SERVICE VERSION 19/udp open|filtered chargen 53/udp closed domain 69/udp closed tftp 79/udp open|filtered finger 111/udp closed rpcbind 123/udp open|filtered ntp 135/udp closed msrpc 137/udp closed netbios-ns 138/udp closed netbios-dgm 161/udp closed snmp 177/udp closed xdmcp 445/udp closed microsoft-ds 500/udp closed isakmp 514/udp open|filtered syslog 520/udp closed route 1434/udp open|filtered ms-sql-m 1900/udp open|filtered upnp 5353/udp closed zeroconf MAC Address: 00:0C:29:33:5D:C2 (VMware) Too many fingerprints match this host to give specific OS details Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 0.89 ms dvwa (192.168.1.105) OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done at Tue Mar 26 04:06:41 2019 -- 1 IP address (1 host up) scanned in 75.85 seconds
- La salida anterior muestra un análisis detallado del escaneo de nmap que se puede utilizar en otras actividades de hacking
- La salida anterior también se puede acceder dentro del directorio de salida de goscan. Como se muestra arriba se puede acceder accediendo a cd./root/.goscan/192.168.105
- Escriba show hosts
[goscan] > show hosts +----------------+--------+---------------------------------------------+------+------------------------------------------------------------------+ | ADDRESS | STATUS | OS | INFO | PORTS | +----------------+--------+---------------------------------------------+------+------------------------------------------------------------------+ | 192.168.1.105 | up | Linux 2.6.17 - 2.6.36 | | * 21/tcp open : ftp [ProFTPD 1.3.2c] | | | | | | * 22/tcp open : ssh [OpenSSH 5.3p1 Debian 3ubuntu4] | | | | | | * 80/tcp open : http [Apache httpd 2.2.14] | | | | | | * 443/tcp open : http [Apache httpd 2.2.14] | | | | | | * 3306/tcp open : mysql [MySQL ] | | | | | | * 19/udp open|filtered: chargen | | | | | | * 53/udp closed : domain | | | | | | * 69/udp closed : tftp | | | | | | * 79/udp open|filtered: finger | | | | | | * 111/udp closed : rpcbind | | | | | | * 123/udp open|filtered: ntp | | | | | | * 135/udp closed : msrpc | | | | | | * 137/udp closed : netbios-ns | | | | | | * 138/udp closed : netbios-dgm | | | | | | * 161/udp closed : snmp | | | | | | * 177/udp closed : xdmcp | | | | | | * 445/udp closed : microsoft-ds | | | | | | * 500/udp closed : isakmp | | | | | | * 514/udp open|filtered: syslog | | | | | | * 520/udp closed : route | | | | | | * 1434/udp open|filtered: ms-sql-m | | | | | | * 1900/udp open|filtered: upnp | | | | | | * 5353/udp closed : zeroconf | | | | | | | +----------------+--------+---------------------------------------------+------+------------------------------------------------------------------+ | 162.241.216.11 | up | DD-WRT v23 (Linux 2.4.36) | | * 21/tcp open : ftp [Pure-FTPd ] | | | | | | * 22/tcp open : ssh [OpenSSH 5.3] | | | | | | * 25/tcp open : tcpwrapped | | | | | | * 26/tcp open : smtp [Exim smtpd 4.91] | | | | | | * 53/tcp open : domain [ISC BIND 9.8.2rc1] | | | | | | * 80/tcp open : http [nginx 1.14.1] | | | | | | * 110/tcp open : pop3 [Dovecot pop3d ] | | | | | | * 139/tcp filtered: netbios-ssn | | | | | | * 143/tcp open : imap [Dovecot imapd ] | | | | | | * 443/tcp open : http [nginx 1.14.1] | | | | | | * 445/tcp filtered: microsoft-ds | | | | | | * 465/tcp open : tcpwrapped | | | | | | * 587/tcp open : smtp [Exim smtpd 4.91] | | | | | | * 993/tcp open : imap [Dovecot imapd ] | | | | | | * 995/tcp open : pop3 [Dovecot pop3d ] | | | | | | * 1720/tcp filtered: h323q931 | | | | | | * 3306/tcp open : mysql [MySQL 5.6.41-84.1] | | | | | | * 5060/tcp filtered: sip | | | | | | * 5432/tcp open : postgresql [PostgreSQL DB ] | | | | | | * 8080/tcp open : http [nginx 1.14.1] | | | | | | * 8443/tcp open : http [nginx 1.14.1] | | | | | | | +----------------+--------+---------------------------------------------+------+------------------------------------------------------------------+
- La consulta anterior muestra los hosts que se escanean y también muestra los puertos que se encuentran utilizando el escáner nmap. Estas pruebas se pueden utilizar para piratear dispositivos IoT
Enumerar
- Esta consulta intentará enumerar los servicios detectados para apuntar
- Teclee enumerate ALL DRY 192.168.1.105
- ALL escaneará automáticamente los servicios abiertos
- FINGER: Este comando intenta encontrar información sobre los usuarios de computadoras.
- HTTP (Protocolo de transporte de hipertexto): este es el protocolo más común utilizado en toda la red. Este protocolo se utiliza para comunicarse con navegadores web y servidores web.
- FTP (Protocolo de transporte de archivos): este protocolo se utiliza para transferir archivos entre el cliente y los servidores.
- SMB (bloque de mensajes de servicio): características de Windows que permiten compartir archivos de forma remota a través de la misma red.
- RDP (Protocolo de escritorio remoto): este protocolo se utiliza para transmitir pantallas de la plataforma basada en Windows
- DRY solo mostrará los comandos y no enumerará el uso de esos comandos
[goscan] > enumerate ALL DRY 192.168.1.105 [] Starting service enumeration [goscan] > [] Starting Enumeration: 192.168.1.105:21 (ftp) [-] To be run: nmap -sV -Pn --script=ftp-anon,ftp-bounce,ftp-libopie,ftp-proftpd-backdoor,ftp-vsftpd-backdoor,ftp-vuln-cve2010-4221 -p21 192.168.1.105 -oA /root/.goscan/192.168.1.105/FTP/192.168.1.105_ftp_nmap_21 [-] Created directory: /root/.goscan/192.168.1.105/FTP [-] [DRY RUN] ftp-user-enum.pl -U /usr/share/wfuzz/wordlist/fuzzdb/wordlists-user-passwd/names/namelist.txt -t 192.168.1.105 > /root/.goscan/192.168.1.105/FTP/192.168.1.105_ftp_user-enum [-] [DRY RUN] hydra -L /usr/share/wfuzz/wordlist/fuzzdb/wordlists-user-passwd/names/namelist.txt -P /usr/share/wordlists/metasploit/unix_passwords.txt -f -o /root/.goscan/192.168.1.105/FTP/192.168.1.105_ftp_hydra -u 192.168.1.105 -s 21 ftp [] Starting Enumeration: 192.168.1.105:80 (http) [-] To be run: nmap -sV -Pn --script=http-vhosts,http-userdir-enum,http-apache-negotiation,http-backup-finder,http-config-backup,http-default-accounts,http-methods,http-method-tamper,http-passwd,http-sitemap-generator,http-auth-finder,http-auth,http-fileupload-exploiter,http-put,http-sql-injection,http-stored-xss,http-xssed,http-php-version,http-unsafe-output-escaping,http-phpmyadmin-dir-traversal,http-ntlm-info,http-phpself-xss,http-open-redirect,http-iis-webdav-vuln,http-form-fuzzer,http-vuln-cve2009-3960,http-vuln-cve2010-0738,http-vuln-cve2010-2861,http-vuln-cve2011-3368,http-vuln-cve2012-1823,http-vuln-cve2013-0156,http-robots.txt,http-wordpress-brute,http-wordpress-enum --script-args http-put.url='/uploads/rootme.php',http-put.file='/root/www/php-reverse.php',basepath='/' -p80 192.168.1.105 -oA /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_nmap [-] [DRY RUN] nikto -host 192.168.1.105 -p 80 > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_nikto [-] [DRY RUN] dirb http://192.168.1.105:80 -o /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_dirb -S -r [-] [DRY RUN] sqlmap -u http://192.168.1.105:80 --crawl=1 > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_sqlmap [-] [DRY RUN] fimap -u "http://192.168.1.105:80" > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_80_fimap [] Starting Enumeration: 192.168.1.105:443 (http) [-] To be run: nmap -sV -Pn --script=http-vhosts,http-userdir-enum,http-apache-negotiation,http-backup-finder,http-config-backup,http-default-accounts,http-methods,http-method-tamper,http-passwd,http-sitemap-generator,http-auth-finder,http-auth,http-fileupload-exploiter,http-put,http-sql-injection,http-stored-xss,http-xssed,http-php-version,http-unsafe-output-escaping,http-phpmyadmin-dir-traversal,http-ntlm-info,http-phpself-xss,http-open-redirect,http-iis-webdav-vuln,http-form-fuzzer,http-vuln-cve2009-3960,http-vuln-cve2010-0738,http-vuln-cve2010-2861,http-vuln-cve2011-3368,http-vuln-cve2012-1823,http-vuln-cve2013-0156,http-robots.txt,http-wordpress-brute,http-wordpress-enum --script-args http-put.url='/uploads/rootme.php',http-put.file='/root/www/php-reverse.php',basepath='/' -p443 192.168.1.105 -oA /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_nmap [-] [DRY RUN] nikto -host 192.168.1.105 -p 443 > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_nikto [-] [DRY RUN] dirb http://192.168.1.105:443 -o /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_dirb -S -r [-] [DRY RUN] sqlmap -u http://192.168.1.105:443 --crawl=1 > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_sqlmap [-] [DRY RUN] fimap -u "http://192.168.1.105:443" > /root/.goscan/192.168.1.105/HTTP/192.168.1.105_http_443_fimap [] Starting Enumeration: 192.168.1.105:3306 (mysql) [-] To be run: nmap -sV -Pn --script=mysql-brute,mysql-databases,mysql-empty-password,mysql-enum,mysql-info,mysql-users,mysql-variables,mysql-vuln-cve2012-2122 -p3306 192.168.1.105 -oA /root/.goscan/192.168.1.105/SQL/192.168.1.105_sql_mysql_nmap_3306 [] Starting Enumeration: 192.168.1.105:22 (ssh) [-] Created directory: /root/.goscan/192.168.1.105/SSH [-] [DRY RUN] hydra -L /usr/share/wfuzz/wordlist/fuzzdb/wordlists-user-passwd/names/namelist.txt -P /usr/share/wordlists/metasploit/unix_passwords.txt -f -o /root/.goscan/192.168.1.105/SSH/192.168.1.105_ssh_hydra -u 192.168.1.105 -s 22 ssh [+] [ALL] Enumeration finished on host: 192.168.1.105 [+] [ALL] Output has been saved at: /root/.goscan
- La consulta anterior muestra que el comando se puede ejecutar en las direcciones IP de destino. La salida anterior muestra que nikto, sqlmap, hydra & fimap se pueden usar para enumerar más el objetivo
- Un análisis más detallado de la herramienta muestra que goscan consume tiempo y utiliza peajes de código abierto en el backend









