ORIGINAL CONTENT: https://noticiasseguridad.com/malware-virus/trump-exe-el-falso-ransomware-que-explota-la-imagen-del-presidente-donald-trump/
El presidente de E.U., Donald Trump, siempre recurre al término ‘fake news’ para referirse a los reportes periodísticos que no le son favorables, y a pesar de las críticas por sus constantes ataques a la prensa, en esta ocasión el término se ajusta perfectamente a la situación reportada por especialistas en forense digital.
Recientemente se han reportado diversos casos de un falso ransomware, con temática de Donald Trump, que se entrega vía email; los operadores de esta campaña buscan engañar a las víctimas mostrando una nota de rescate para obtener ganancias por descifrar archivos que en realidad nunca estuvieron cifrados.
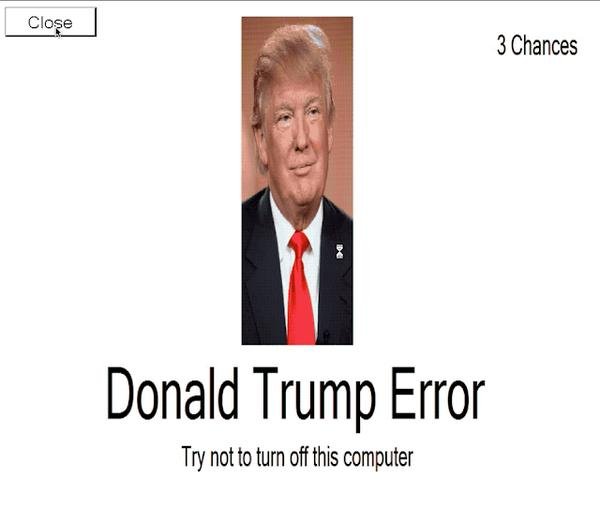
Cuando el supuesto ransomware se instala en las computadoras de las víctimas (gracias al archivo trump.exe), los hackers bloquean la computadora objetivo y muestran sólo una imagen de Trump, además de la nota de rescate característica en todas las infecciones de ransomware.
Los expertos en forense digital de la firma de investigación de malware Cisco Talos Intelligence mencionan que han acumulado múltiples evidencias sobre este falso ransomware. Un reporte firmado por el experto Nick Biasini, de Cisco, menciona: “Las muestras recolectadas no cifran los datos de las víctimas, o en algunos casos sólo lo hacen de forma parcial y deficiente. El principal objetivo es engañar a los usuarios, haciéndoles creer que su información se ha bloqueado o perdido por completo, lo que los fuerza a pagar un rescate siendo que su pantalla sólo fue bloqueada”.

Además de la imagen del presidente Trump, los operadores de esta campaña también están utilizando la imagen del presidente de Rusia, Vladimir Putin, para bloquear las pantallas de cientos de víctimas y mostrar un mensaje amenazante: “Su PC ha sido bloqueada por el locker PuTiN”, o algún mensaje similar. En estos ataques, el fondo de pantalla de las víctimas también es modificado, mostrando un patrón de calaveras en llamas.
Después de completar su instalación, este malware con temática de Putin bloquea la pantalla de las víctimas, elimina los íconos del escritorio y la barra de tareas, además del administrador de tareas. Posteriormente se muestra a las víctimas el medio de contacto para acordar un pago con los hackers.
Aunque la investigación sigue en curso, los expertos en forense digital plantean que es probable que estas infecciones comiencen a través de campañas masivas de spam en redes sociales y vía email. “Las víctimas potenciales son expuestas a falsos anuncios o emails relacionados con la prevención de fraudes bancarios; algunos de estos mensajes son enviados por un supuesto ejecutivo de prevención de riesgos de compañías como Visa”, mencionan los expertos.
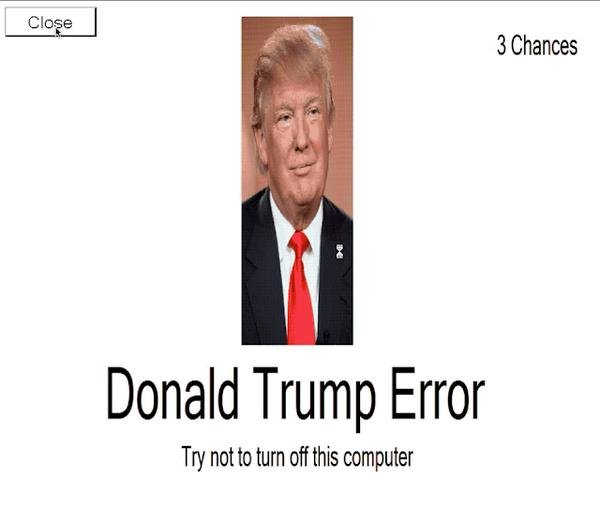
Hace algunos meses se detectaron múltiples casos de infección con locker malware que usaba la imagen de Trump (conocido como Error Donald Trump), aunque aún se desconocen mayores detalles sobre sus desarrolladores y objetivos.
Como mencionan especialistas en forense digital del Instituto Internacional de Seguridad Cibernética (IICS), la proximidad de las elecciones presidenciales de 2020 en E.U. hacen mucho más probable que los usuarios de tecnología se conviertan en víctimas de estafas por Internet que involucran el uso de temáticas políticas.