ORIGINAL CONTENT: https://www.securitynewspaper.com/2019/10/04/hackers-invested-only-160-usd-in-a-phishing-campaign-that-infected-over-70k-victims-how-did-they-do-it/
Information security specialists have revealed details about a recent cybercriminal campaign identified as “MasterMana Botnet”, related to multiple key concepts in the world of cybersecurity, such as the use of botnet, backdoors, theft of cryptocurrency, among others. Experts estimate that thousands of companies around the world have already been attacked by the operators of this campaign at a very low cost.
According to specialists from security firm Prevailion, this campaign began in late 2018, with operators sending phishing emails indiscriminately to thousands of public and private organizations around the world.
The phishing emails used by the attackers were designed to extract information related to cryptocurrency addresses from unsuspecting users. Information security experts mentioned that, based on the methods used in this campaign, it is possible to link it to the hacker group known as “Gorgon Group”, active for almost a decade.
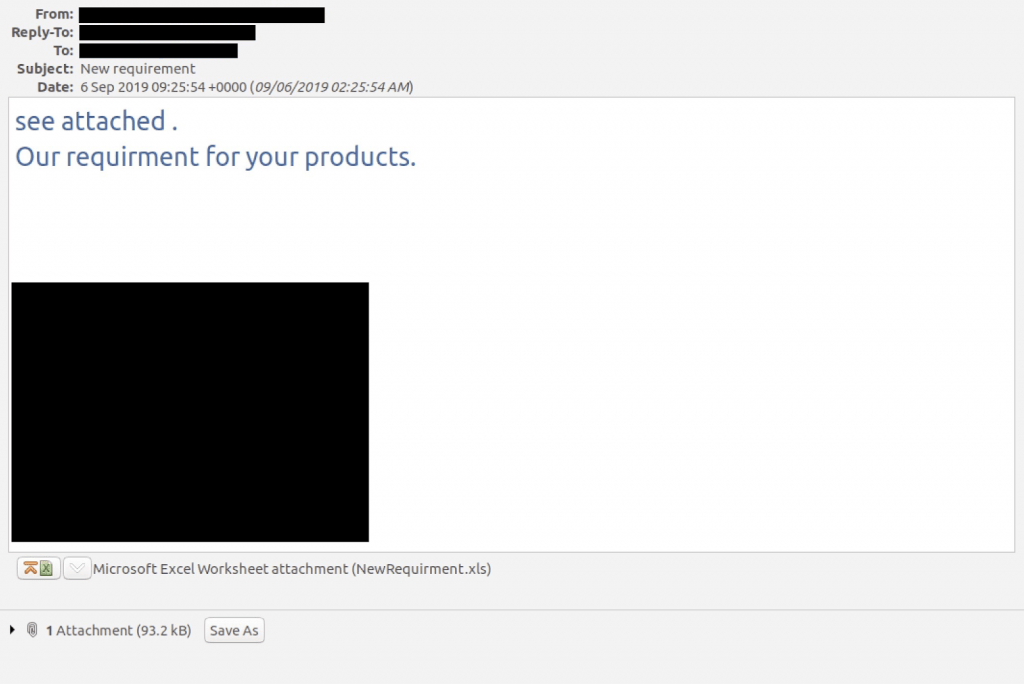
After the victims opened the malicious email, an attachment loaded with malware appeared. Opening this document triggered the attack, which had an approach that allowed it to evade detection of antivirus tools due to the use of third-party sites, such as Bitly, Blogspot and Pastebin instead of just using web domains controlled by hackers. The methods used by hackers also allowed them to bypass automated detection systems such as sandbox environments.
Azorult, one of the Trojans used by hackers, was designed to extract user names, browsing history, website cookies and cryptocurrency online wallets. In addition, this Trojan was also able to list hosts, upload and download files and even take screenshots of the infected computer, mentioned information security specialists.
Another purpose of using third-party sites is cost reduction. On average, the rent of virtual private servers (VPS) costs $60 USD, plus any version of Azorult available on dark web hacking forums costs about $100 USD, so deploying this hacking campaign cost no more than $200.
“It’s ironic to think of companies investing hundreds, or even thousands of dollars in security solutions, while threat actors can deploy a massive phishing campaign with just a few bucks; we can’t even see this campaign as an advanced persistent threat,” the experts say.
While activity associated with this campaign has been reduced, researchers believe it is highly likely that this group of cybercriminals will continue their operations in the future, so organizations should not fail to pay attention to attack vectors such as the phishing emails.
Information security specialists at the International Institute of Cyber Security (IICS) mention that MasterMana Botnet is the perfect example that hackers don’t need to use the most sophisticated tools, because they know that using techniques like phishing they can access a system via the weakest link in the information security chain: the human factor.
Preventing such attacks requires a comprehensive strategy, where system administrators are able to implement various security methods, such as firewalls, email filters, and antivirus software, while keeping training to any member of the organization who uses computer equipment with an Internet connection in order to minimize exposure to any social engineering campaign.






0 comments:
Post a Comment