ORIGINAL CONTENT: https://www.securitynewspaper.com/2019/09/27/new-permanent-jailbreak-for-any-iphone-from-4-to-x-now-available/
The number of jailbreaks for iOS devices has declined markedly over the more recent years, although they continue to appear; last month, for example, a flaw in an Apple update allowed a jailbreak for the latest iPhone models. Now, an ethical hacking specialist has announced a supposed functional exploit to permanently jailbreak any iPhone between the 4 and iPhone X.
Through Twitter, the axi0mX user posted “checkm8”, their iPhone exploit, mentioning that with a little more work, this exploit could generate a jailbreak, so it could be an important revelation.
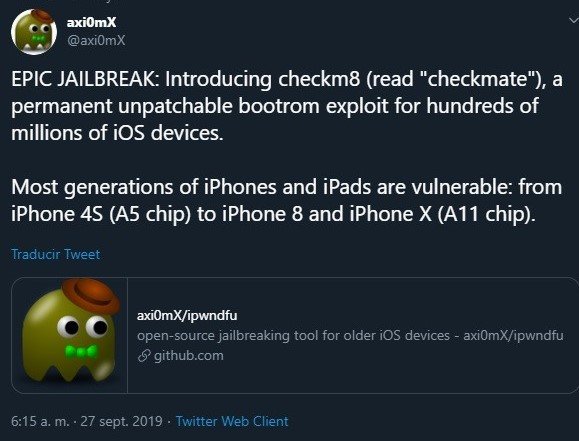
“This is not a complete jailbreak with Cydia, it’s just an exploit,” the ethical hacking expert says. “It is possible to use checkm8 to dump SecureROM, decrypt keybags with the AES engine, and degrades a device to enable JTAG, which requires additional hardware and software,” mentions the anonymous expert.
Other exploit features also include:
- Jailbreak and downgrade iPhone 3GS
- Pwned DFU Mode with steaks4uce exploit for S5L8720 devices
- Pwned DFU Mode with limera1n exploit for S5L8920/S5L8922 devices
- Pwned DFU Mode with SHAtter exploit for S5L8930 devices
- Dump SecureROM on S5L8920/S5L8922/S5L8930 devices
- Dump NOR on S5L8920 devices
- Flash NOR on S5L8920 devices
- Encrypt or decrypt hex data on a connected device in pwned DFU Mode using its GID or UID key
Furthermore, axi0mX emphasizes that its exploit cannot be used remotely, as it requires USB connection. Just over a year ago, during the iOS 12 beta testing period, Apple fixed a critical use-after-free vulnerability in the iBoot USB code. According to experts in ethical hacking, the flaw can only be exploited via USB and depends on physical access to the devices; “It’s not possible to exploit it any other way,” the expert says.
Even though this patch leading to the exploit is easy to find, the researcher points out that this is a very complex vulnerability to exploit on most devices. “At least two other researchers have found a way to exploit this vulnerability; finding the patch is relatively simple, the hard part is exploiting the flaw,” adds the expert.
On the GitHub page where the exploit is published, the expert mentions: “The tool is currently in beta and in certain circumstances could lock a device. It will try to save a copy of the data in NOR in the nor-backups folder before upgrading the new data to NOR, and will not attempt to overwrite the critical data in NOR that your device needs to function. If something goes wrong, hopefully you will be able to restore the latest version of IPSW in iTunes and try to reset all the features on your device, or use nor backups to restore NOR to the original state, but I can’t provide any guarantees,” adds the expert.
Due to the complexity of trying to create this permanent jailbreak, ethical hacking specialists from the International Institute of Cyber Security (IICS) do not recommend trying to run this exploit unless you have the necessary knowledge.






0 comments:
Post a Comment